Security and Governance for your Business Applications
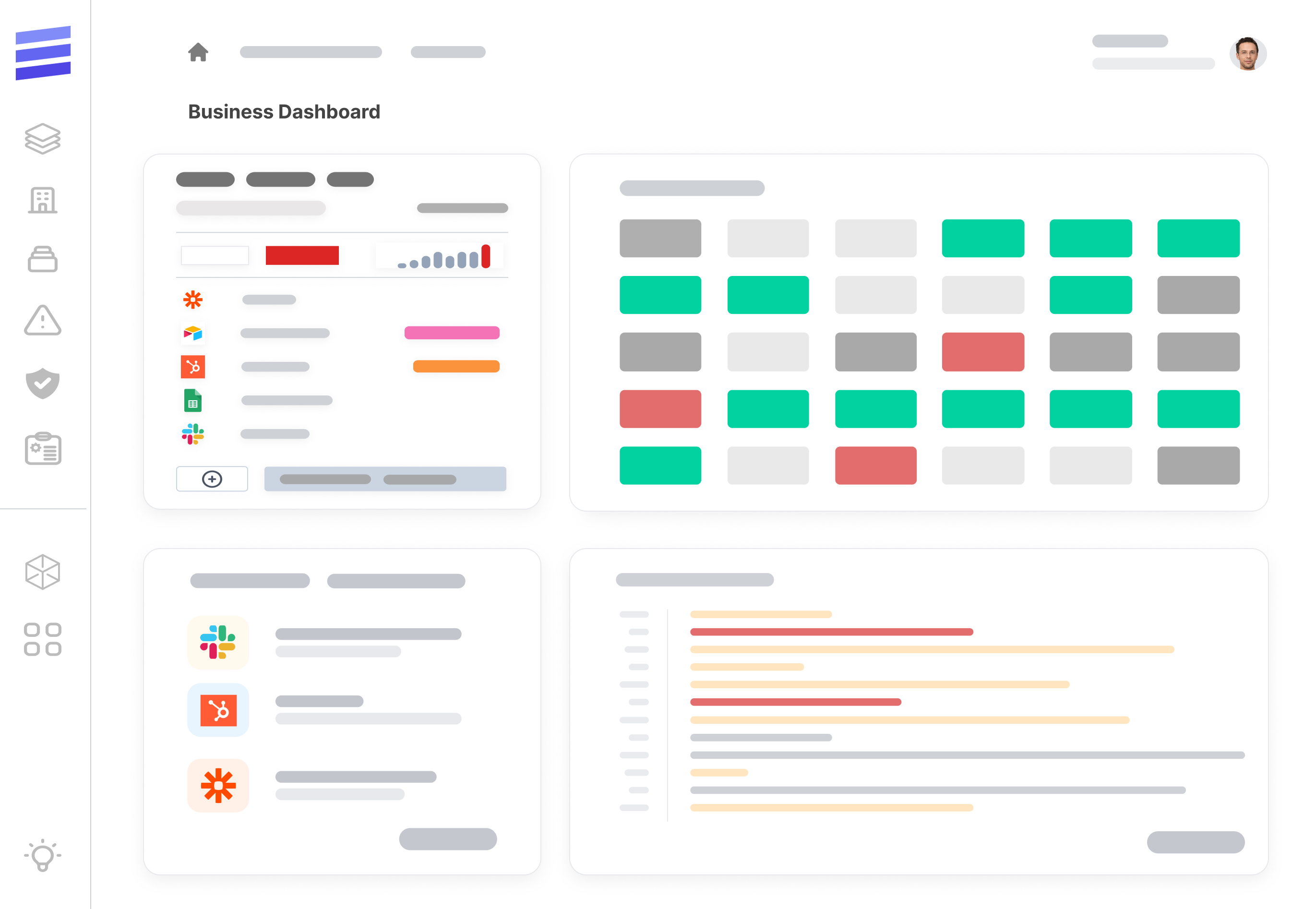
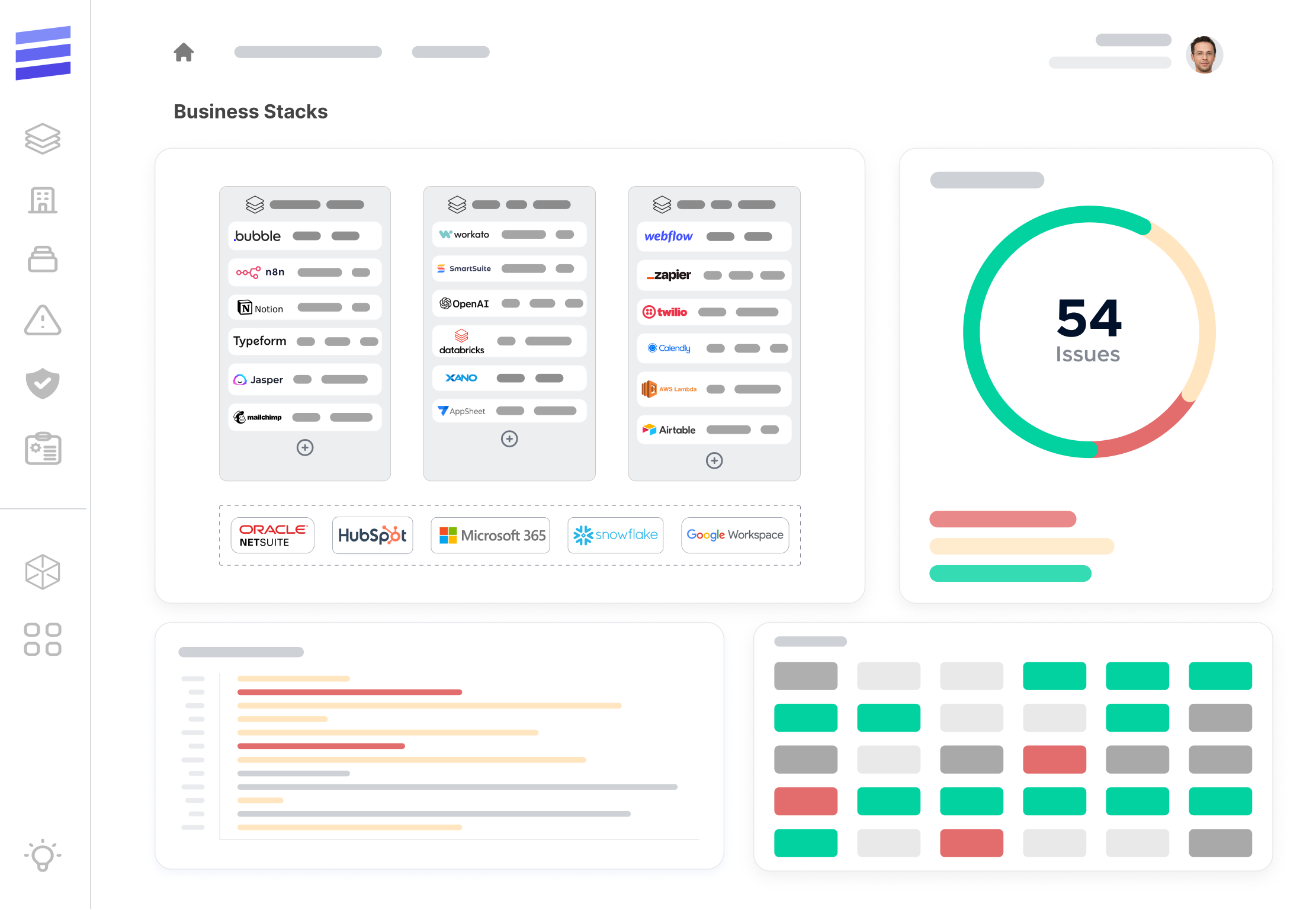
TrustedStack™ is a powerful Business Applications Governance tool helping CIO, CSO, GRC, CTO, and Ops teams to effectively manage the security and compliance of business applications that were built using low-code/no-code (LCNC), automation, AI and other technologies.
Get Started